A Web Application Firewall is a security tool that protects web applications and APIs from malicious requests and cyber attacks. WAFs are a critical defense for enterprises and online businesses that need to protect sensitive data.
WAFs work by analyzing each HTTP/S request and blocking or filtering out any malicious requests. WAFs can also help with load balancing and provide visibility into web traffic.
WAFs help protect against cross-site scripting (XSS), SQL injection and cookie poisoning. Such vulnerabilities often serve as the primary entry points for breaches, providing attackers with access to your organization’s most sensitive data.
WAFs protect against all types of attacks on the OWASP Top 10 list, and a good WAF must also protect against unknown and zero-day attacks that go beyond the OWASP Top 10.
This is part of an extensive series of guides about information security.
Vea este episodio de Radware Minute con Uri Dorot, de Radware, para saber qué es un firewall de aplicaciones web, por qué es importante tener uno, cómo funciona y qué debe buscar al elegir uno.
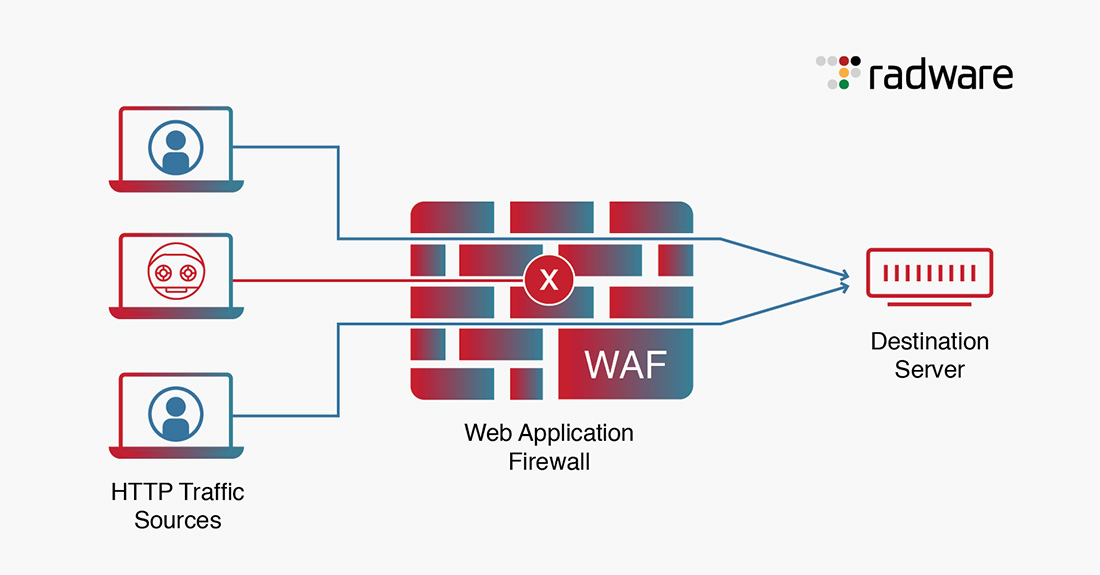
Figure 1: Basic WAF Architecture.
Cuando se implementa un WAF frente a una aplicación web, se coloca un escudo protector entre la aplicación web e Internet que supervisa todo el tráfico entre la aplicación y el usuario final.
A WAF protects web apps by filtering, monitoring and blocking any malicious HTTP/S traffic traveling to the web application, and also prevents any unauthorized data from leaving the application by adhering to a set of policies that help determine what traffic is malicious and what traffic is safe.
Al igual que un servidor proxy actúa como intermediario para proteger la identidad de un cliente, en una implementación tradicional, un WAF funciona de forma similar pero a la inversa (llamado proxy inverso), actuando como intermediario que protege al servidor de la aplicación web de un cliente potencialmente malicioso.
Web application firewalls (WAFs) typically employ three security models:
- Positive Security Model (Allowlisting): This approach leverages machine learning and behavior modeling algorithms to identify legitimate traffic. It denies all requests by default and only allows those that are known to be trusted. This method is less resource-intensive than the negative security model and provides a list of IP addresses that are known to be safe. However, the downside is that it requires a learning period to establish baselines of legitimate behavior and if not tuned properly could unintentionally block benign traffic.
- Negative Security Model (Blocklisting): This method is based on up-to-date signatures against known vulnerabilities. It defines the type of traffic that the WAF denies, while the rest is accepted. This approach is good if you have complete knowledge of all vulnerabilities that could exist for a single product. However, it requires constant updates to blocklist the next threats.
- Hybrid Approach: This approach combines the strengths of both the positive and negative security models. It uses a combination of allow and block lists to determine what gets through. Some WAFs take a hybrid approach by using allow lists, but add in a secondary layer of blocklist checking for the most common types of attacks. This approach provides security coverage against both known and unknown potential threats.
Learn more in our detailed guide to web application firewall architecture.
There has been a 171% year-on-year increase in malicious web application transactions from 2022 to 2023, a steep rise compared to the 128% rise from 2021 to 2022.
In response to these threats, the Web Application Firewall (WAF) market is evolving rapidly, driven by several key trends:
-
Democratization of AI Tools: The latest advancements in AI and the democratization of generative AI tools have made malicious scripts and injections easily available for any wannabe hacker. This has led to a surge in the number of attack attempts and more sophisticated attacks.
-
Integration with Other Systems: WAF providers are continuously improving their offerings by integrating their products with other systems such as Security Information and Event Management (SIEM) systems, Application Security Testing (AST), and Web Access Management (WAM). This integration allows for a more comprehensive security approach, enhancing the ability to detect and respond to threats.
-
Use of AI in Detection, Monitoring, Analytics, and Mitigation Engines: Vendors are developing WAF solutions based on a positive security model that utilizes machine learning algorithms to analyze HTTP requests. This advanced technology helps in accurately identifying and mitigating potential threats, thereby enhancing the overall security posture.
-
Increase in IoT Devices: The proliferation of internet of things (IoT) devices has led to an increased focus on data privacy norms. Organizations are likely to invest in WAF solutions that offer IoT-specific features such as device fingerprinting and protocol validation to ensure compliance and enhance security.
-
Demand for Enhanced Threat Intelligence: Enterprises are seeking WAF solutions that provide enhanced threat intelligence, extended protection, and a variety of out-of-the-box integrations. These features enable organizations to better understand the threat landscape and respond effectively to potential attacks.
-
Focus on New Detection Methods: There is a growing focus on developing new detection methods to prevent web attacks and minimize false positives. This not only improves the accuracy of threat detection but also reduces the chances of legitimate traffic being blocked.
-
Consolidation of Solutions and Transition from WAF to WAAP: The market is witnessing a trend towards the consolidation of solutions, moving towards a single pane of glass approach. This involves transitioning from traditional WAF solutions to web application and API protection (WAAP), which provides a more comprehensive and modernized approach to application security.
Related content: Read our guide to WAF testing.
A WAF can be implemented in various ways. There are three primary types of WAF:
1. Network-based WAF
This is generally a hardware-based solution that is installed locally on the network infrastructure. It offers low latency and high performance, which is crucial for real-time applications. However, it is also expensive and requires physical maintenance. In most cases these devices are self-maintained and configured which requires internal resources and a certain level of knowledge. Network-based WAFs are typically used by large organizations that have the resources to manage and maintain the physical equipment.
2. Software-based WAF
This type of WAF is managed by a service provider that offers the WAF on a "security-as-a-service" basis. Software-based WAFs provide additional customization options and are typically less expensive than network-based WAFs. However, their filtering and monitoring processes may be slower, as they are run on top of a virtual machine. These WAFs can be deployed for different servers, offering a lot of flexibility.
3. Cloud-based WAF
Cloud-based WAFs offer an affordable and easy-to-implement option. They usually offer a turnkey installation that is as simple as a change in DNS to redirect traffic. Los WAF basados en la nube también tienen un costo inicial mínimo, ya que los usuarios pagan mensual o anualmente por la seguridad como servicio. They can offer a solution that is consistently updated to protect against the newest threats without any additional work or cost on the user’s end. Some Cloud WAF vendors offer managed services that can remotely assist with configuring and managing the WAF. El inconveniente de un WAF basado en la nube es que los usuarios ceden la responsabilidad a un tercero. This means that some WAF features can be a “black box” for them.
Inline vs. Out of Path (OOP)
Lo ideal es que un WAF ofrezca la opción de implementarse en línea, donde la solución puede servir como "intermediario", o como un servicio fuera de ruta (OOP) basado en API. Una implementación OOP basada en API puede ofrecer varias ventajas únicas que le permiten ser optimizada para entornos multi-cloud. Permite que las peticiones de las aplicaciones vayan directamente del cliente al servidor de aplicaciones sin interrupción. Benefits include reduced latency, no traffic redirection and no need for SSL certificate sharing, increased uptime, and comprehensive protection across heterogeneous environments.
A traditional firewall and a web application firewall (WAF) serve different, but complementary, roles in the realm of cybersecurity.
A network firewall operates primarily at the network and transport layers (layers 3 and 4 of the OSI model). Its primary function is to separate a secure zone from a less secure zone and control communications between the two. It acts as a barrier that prevents unauthorized access to the network as a whole. Network firewalls handle lower layers and are typically associated with protecting the network infrastructure. They monitor and control incoming and outgoing network traffic based on predetermined security rules.
A WAF provides protection at the application layer (layer 7 of the OSI model). A WAF protects web applications by monitoring and guarding Hypertext Transfer Protocol (HTTP) traffic. It sits between external users and web applications to analyze all HTTP communication. It then detects and blocks malicious requests before they reach users or web applications. As a result, WAFs secure business-critical web applications and web servers from zero-day threats and other application-layer attacks.
In essence, while a network firewall provides a first line of defense against a broad range of threats to the network and data centers, a WAF offers specialized, application-level protection to detect and block a variety of threats specific to web applications.
When comparing a Web Application Firewall (WAF), Intrusion Prevention System (IPS), and Next-Generation Firewall (NGFW), it's important to understand that they each focus on different aspects of protection:
- WAF (Web Application Firewall): A WAF primarily secures web applications by filtering and monitoring HTTP/S traffic at the application layer (Layer 7 of the OSI model). It is specifically designed to detect and block threats targeting web applications, like the OWASP Top 10.
- IPS (Intrusion Prevention System): An IPS focuses on detecting and preventing attacks at the network level (typically Layers 3 and 4). It analyzes network traffic for signs of known vulnerabilities and exploits, such as buffer overflows, protocol violations, and brute force attacks. It lacks the deep application-layer protection that a WAF provides.
- NGFW (Next-Generation Firewall): An NGFW combines traditional firewall capabilities with advanced features like deep packet inspection, intrusion prevention (IPS), and application awareness. It protects both network and application traffic by filtering based on security policies and detecting advanced threats. NGFWs try to balance between IPS-like network protection and some WAF-like application-layer security, but they don’t offer the same level of protection, visibility, granularity or customization for web application threats that a dedicated WAF provides.
Learn more in our detailed guide to WAF vs IPS.
Here are some of the key capabilities a WAF should have:
Dual Security Models
WAF should ideally combine both positive and negative security models. This combination allows the WAF to mitigate known web application attacks, such as access violations, attacks disguised behind Content Delivery Networks (CDNs), API manipulations and assaults, HTTP/S floods, brute force assaults, and others. Además, esta combinación también proporciona protección contra ataques y vulnerabilidades desconocidas, como los ataques de día cero.
Deep and Complete Coverage of the OWASP Top 10: A WAF should provide extensive security coverage that includes all the vulnerabilities listed in the OWASP Top 10. This ensures that the most critical security risks to web applications are well protected.
Protection Beyond the OWASP Top 10: In addition to covering the OWASP Top 10, a WAF should also provide protection against unknown and zero-day attacks. This means that the WAF should be capable of securing web applications from threats that are not yet known or have not been previously encountered.
API Discovery and Protection
A WAF should provide API discovery and protection that offers visibility, enforcement and mitigation of all forms of API abuse and manipulation, whether for on-premises or cloud-hosted environments. It should cover the OWASP Top 10 API Security Risks. As many of those risks are associated with the application business logic, it should be able to map the application API business logic and mitigate BLA in real-time.
Integration with Bot Management Solutions
A WAF should have the ability to integrate with bot management solutions to detect and mitigate sophisticated, human-like bots.
Real-Time Policy Optimization
A WAF should leverage behavioral-based, AI and machine-learning algorithms to create and optimize security policies in real-time. This capability ensures comprehensive protection while producing minimal to no false positives. It also provides automatic detection and protection of new applications as they are added to a network.
Core Features
The core features of a WAF should include the ability to filter network and application traffic based on geo-blocking, IP groups, blocklists, allowlists, whitelisting and blacklisting.
Built-In DDoS Protection
To counter application-layer DDoS attacks, a WAF should have built-in DDoS protection.
Client-side Protection: A WAF should also include client-side protection to secure end users from attacks embedded in the application supply chain. This extends the protection against supply-chain attacks via third-party APIs to offer protection against attacks that do not go through the server and are thus not detected by traditional WAFs. This capability is required to adhere to several compliance standards such as PCI DSS 4, NIS2, and DORA.
Data Leakage Prevention Mechanisms
To protect sensitive user data, such as personally identifiable information (PII), a WAF should have data leakage prevention mechanisms.
Learn more in our detailed guide to WAF security.
IP Fencing
IP fencing, also known as IP allowlisting or blocklisting, is a technique where a WAF restricts access to a web application based on the client's IP address. This method allows administrators to define a list of trusted IP addresses that are allowed to access the application, while blocking traffic from unknown, untrusted, or malicious IPs.
This can be particularly effective in preventing attacks from known malicious actors, such as those operating from IP ranges associated with botnets or cybercriminal groups. IP fencing is often used to protect internal systems by allowing access only from internal or VPN-secured IP addresses. While this method is useful for blocking large-scale attacks from specific regions or networks, it may not be sufficient for sophisticated attackers using techniques like IP spoofing or rotating through large pools of IP addresses.
Geo-Fencing and Geo-Blocking
Geo-fencing and geo-blocking are methods that limit access to a web application based on the geographical location of the user, which is determined by analyzing their IP address. Geo-fencing creates virtual boundaries, allowing or denying traffic from specific regions. For example, if an organization only serves customers in North America, they can block traffic from other continents, reducing their attack surface.
Geo-blocking, which is more aggressive, denies traffic from entire regions or countries known for a high frequency of cyber-attacks. However, these methods should be used with caution as attackers may use proxy servers or VPNs to mask their true location, bypassing geo-based restrictions.
Request and Response Inspection
Request and response inspection involves analyzing the data in both incoming requests and outgoing responses between the web application and the user. This method allows the WAF to monitor for malicious content or behavior embedded in HTTP/S requests, such as SQL injection attempts, cross-site scripting (XSS), Server-side Request Forgery (SSRF), or other forms of code injection.
The WAF inspects parameters, headers, cookies, and the body of the request to ensure they adhere to security policies and do not contain malicious payloads. Similarly, the WAF inspects responses to detect sensitive data leakage, such as unintentional exposure of personal information, authentication tokens, or server configuration details. By performing deep packet inspection on both ends of the communication, the WAF ensures that attacks are blocked before they can be executed, and sensitive information is protected from being exposed to attackers.
Security Rules
Security rules are a core WAF functionality, defining specific criteria that determine which traffic should be allowed or blocked. These rules can be based on various factors such as known attack patterns (e.g., SQL injection, XSS), anomalies in HTTP request headers, malformed requests, or even the presence of specific keywords or character sequences that are indicative of an attack.
Most WAFs come preloaded with rulesets designed to address common vulnerabilities and exploit techniques as identified by organizations like OWASP (e.g., OWASP Top 10 vulnerabilities). However, administrators can also create custom rules tailored to the unique needs of their application, such as blocking requests to sensitive endpoints or enforcing strict validation on user input fields. A WAF should continuously update its ruleset to account for new attack techniques, zero-day vulnerabilities.
Anomaly Scoring
Anomaly scoring is an advanced technique that assigns numerical scores to individual requests based on how closely they match malicious behavior patterns. Each suspicious activity or deviation from normal traffic-such as sending unusually large payloads, accessing unexpected resources, or attempting to exploit known vulnerabilities-adds to the anomaly score. When a request's cumulative score surpasses a predefined threshold, the WAF treats it as malicious and blocks it from reaching the application.
This method is particularly valuable in detecting sophisticated or zero-day attacks that do not match any known attack signatures but exhibit unusual patterns. Anomaly scoring allows the WAF to "learn" what typical, legitimate traffic looks like over time, improving its ability to detect outliers and potential threats without relying solely on static rules. This adaptive capability is crucial for defending against new and evolving threats that are not covered by predefined rule sets.
Inteligencia sobre amenazas
Threat intelligence is a proactive method used by WAFs to enhance security by leveraging real-time data on emerging threats from external sources. By integrating threat intelligence feeds, a WAF can automatically update its defenses based on the latest information about known malicious IP addresses, domains, botnets, and attack vectors. These intelligence feeds are continuously updated by security researchers, vendors, and global cybersecurity communities, providing insights into new vulnerabilities, zero-day exploits, and cyberattack trends.
For example, if a new vulnerability is discovered in widely used software, a threat intelligence feed can immediately inform the WAF, enabling it to block any attempts to exploit that vulnerability before a patch is even released. Additionally, threat intelligence can help identify large-scale, coordinated attacks, such as DDoS campaigns or botnet-driven attacks, and enable the WAF to take preventive action by blocking traffic from malicious sources.
Auto Blocking of Malicious Sources
Auto blocking of malicious sources is another proactive technique that enhances web application security by automatically identifying and blocking harmful IP addresses based on observed attack patterns and behaviors. A unique, industry-first approach to this is the AI-based Correlation Engine in Radware's Cloud Application Protection solution leverages a sophisticated correlation engine to analyze incoming security events across different protection modules (such as WAF, API protection, and bot management) and assigns penalty scores to sources involved in malicious activities. Once a source's penalty score crosses a predefined threshold, it is temporarily blocked across all applications within the account.
This automated, real-time blocking mechanism ensures that malicious traffic is promptly filtered out, preventing attacks before they can reach critical systems. Auto blocking reduces server load and minimizes overheads associated with processing malicious requests, thereby strengthening the overall security posture of the application environment.
Learn more in our detailed guide to most reliable web application firewalls.
In today's digital landscape, the need for a web application firewall (WAF) has become more critical than ever. Here are several reasons why you need a WAF:
Compliance Requirement: In many verticals today, having a WAF is not just a security best practice—it’s a compliance requirement. Regulatory standards such as PCI DSS and NIS2 mandate the use of a WAF to protect against web application attacks.
Agile Development Methodologies: While these methodologies allow for rapid development and deployment, they can also introduce new vulnerabilities into web applications if not properly managed. A WAF can provide the necessary security controls to mitigate these risks.
Shift to the Cloud: As more organizations move their operations to the cloud, they must also contend with the unique security challenges that this environment presents. A WAF can provide consistent security policies across on-premises and cloud environments.
Increased Use of Web-Based Software or SaaS Applications: These applications can be targeted by attackers due to their widespread use and internet-facing nature. A WAF can protect these applications by filtering, monitoring, and analyzing HTTP and HTTPS traffic.
Volume and Diversity of Attacks: With the increasing volume and diversity of web application attacks, it’s virtually impossible to protect applications without a WAF. A WAF protects web applications from a wide range of attacks such as cross-site forgery, server-side request forgery, file inclusion, and SQL injection, among others. It also safeguards applications and websites against the most critical security vulnerabilities (visit OWASP Top 10 to see the full list) including, but not limited to:
- Injection Attacks: This category includes both cross-site scripting (XSS) and SQL Injection attacks. In these types of code injection attacks, adversaries insert malicious scripts or SQL statements into a legitimate website or web application’s database query software. This can potentially allow the attacker to steal sensitive information, impersonate the user, or modify or delete information in the database.
- Security Misconfiguration: This category includes various types of attacks that exploit misconfigurations in web applications, including some forms of application-layer DDoS attacks.
- Vulnerable and Outdated Components: This category addresses risks associated with using components with known vulnerabilities, which can be exploited by attackers.
Remote Workforces: The shift to remote work has expanded the attack surface for many organizations, as employees access corporate resources from various locations and devices. A WAF can provide the necessary security controls to protect these remote access points.
In addition to the above, it's important to consider zero-day attacks, which occur when a hacker discovers and exploits a previously unknown vulnerability in a software application before the software developer has had a chance to create and distribute a patch. There are two perspectives to consider when discussing zero-day attacks:
- Exploitation of Zero-Day Vulnerabilities: This is when an attacker exploits a vulnerability that is not yet known to the public or the vendor.
- Unrecognized Attacks by Current Defense Systems: From the perspective of protection solutions such as WAF, DDOS and bot mitigation, a zero-day attack can also refer to an attack that the current defense system doesn’t recognize as an attack because there is no signature for it yet.
By incorporating a WAF into their security infrastructure, organizations can significantly enhance their ability to defend against these and other application-level attacks. This can help protect sensitive data, maintain application availability, and ensure compliance with various regulatory standards.
Learn more in our detailed guide to web application firewall services.
Alteon Integrated WAF
Radware’s Alteon Integrated WAF ensures fast, reliable and secure delivery of mission-critical Web applications and APIs for corporate networks and in the cloud. Recommended by the NSS, certified by ICSA Labs, and PCI compliant, this WAF solution combines positive and negative security models to provide complete protection against web application attacks, access violations, attacks disguised behind CDNs, API manipulations, advanced HTTP attacks (such as slowloris and dynamic floods), brute force attacks on log-in pages, and more.
Cloud WAF
Radware’s Cloud WAF service is part of our Cloud Application Protection Service which includes WAF, API protection, Bot management, Layer-7 DDoS protection and Client-Side Protection. The service analyzes web apps to identify potential threats, then automatically generates granular protection rules to mitigate those threats. It also offers device fingerprinting to help identify bot attacks, AI-powered API discovery and protection to prevent API abuse, full coverage of OWASP Top 10 vulnerabilities, and data leak prevention, which prevents the transmission of sensitive data. Radware Cloud WAF is NSS recommended, ICSE Labs certified, and PCI-DSS compliant.
Kubernetes WAF
Radware Kubernetes WAF is a comprehensive and scalable web application firewall designed for CI/CD environments orchestrated by Kubernetes. It provides robust data and application protection, integrating seamlessly with Kubernetes orchestration and common DevOps tools. The solution offers advanced automation, autoscaling, and elasticity, ensuring security for microservices architectures. It combines both negative (signature-based) and positive security models to protect against known and unknown threats, including zero-day attacks. Additionally, it provides detailed visibility and analytics for DevSecOps teams, reducing total cost of ownership with minimal false positives.
Servicios de protección de aplicaciones en la nube
Radware’s Cloud Application Protection Services provide a unified solution for comprehensive web application and API protection, bot management, client-side protection, and application-level DDoS protection. Leveraging Radware SecurePath™, an innovative API-based cloud architecture, it ensures consistent, top-grade security across any cloud environment with centralized visibility and management. This service protects digital assets and customer data across on-premise, virtual, private, public, and hybrid cloud environments, including Kubernetes. It addresses over 150 known attack vectors, including the OWASP Top 10 Web Application Security Risks, Top 10 API Security Vulnerabilities, and Top 21 Automated Threats to Web Applications. The solution employs a unique positive security model and machine-learning analysis to reduce exposure to zero-day attacks by 99%. Additionally, it distinguishes between “good” and “bad” bots, optimizing bot management policies to enhance user experience and ROI. Radware’s service also ensures reduced latency, no route changes, and no SSL certificate sharing, providing increased uptime and seamless protection as businesses grow and evolve.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.